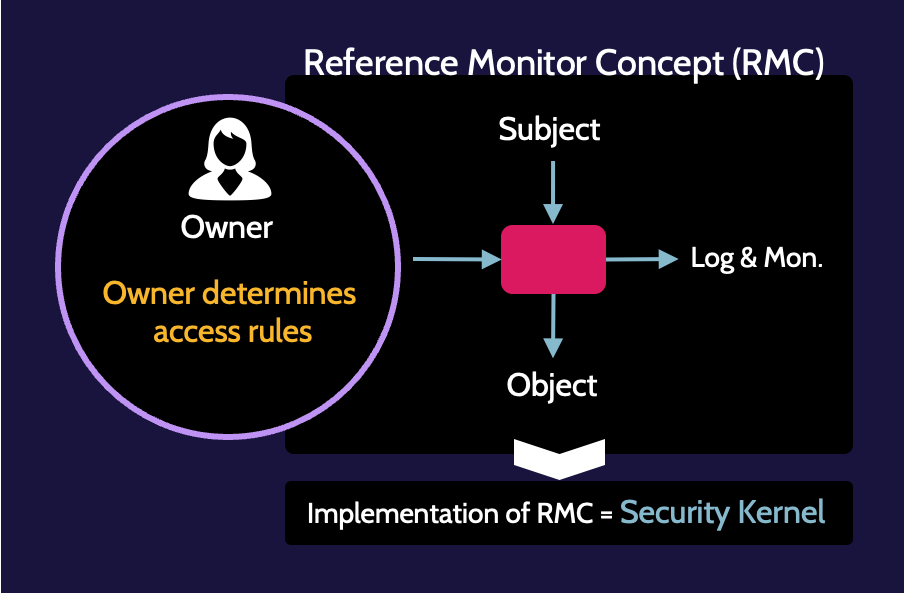
Home gateway operating model using reference monitor for enhanced user comfort and privacy | Semantic Scholar

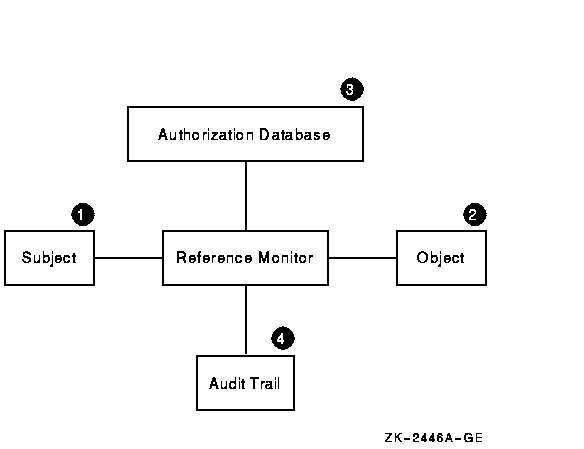
A system's security architecture. The reference monitor intercepts each... | Download Scientific Diagram
GitHub - Sanket-MSD/Reference-Monitor: Reference Monitor for Access Control monitoring. This is a part of Information, Security and Privacy coursework at NYU

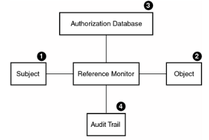
Reference Monitor Pattern. Authorization rules indicate a collection of... | Download Scientific Diagram
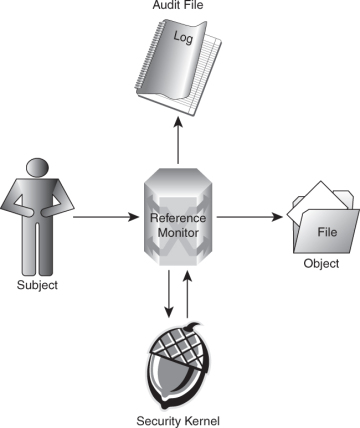
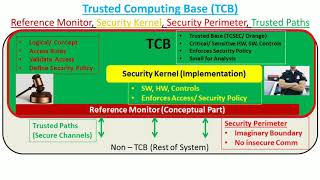
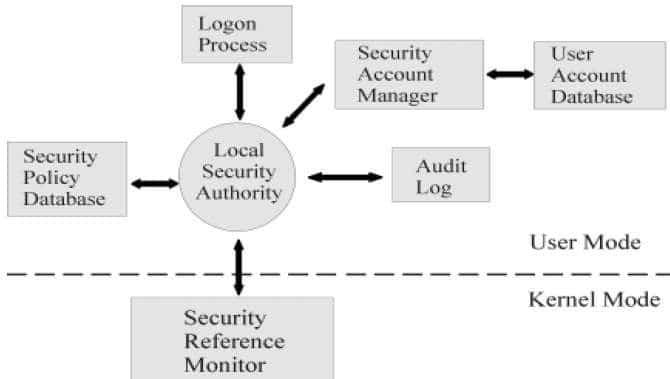
Security Architecture | CISSP Exam Cram: Security Architecture and Models | Pearson IT Certification

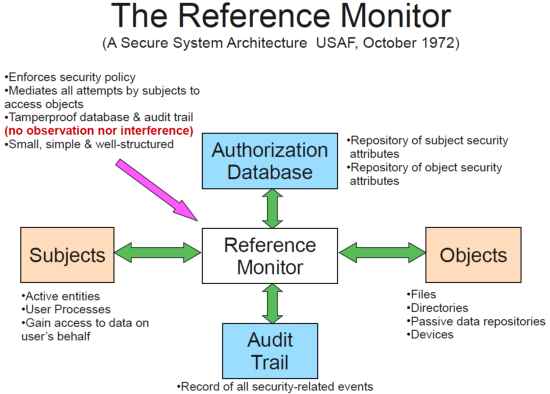
1 Title Goes Here Understanding Authentication and Access Control in Distributed Systems Mike Reiter University of North Carolina at Chapel Hill. - ppt download

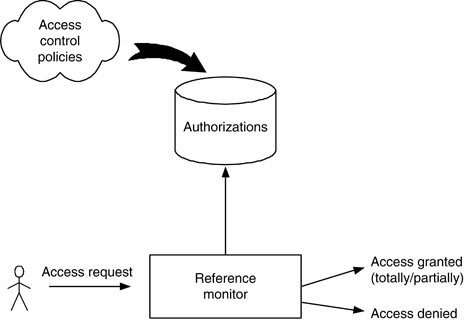
Authentication and authorization Access control consists of two steps, authentication and authorization. Subject Do operation Reference monitor Object. - ppt download